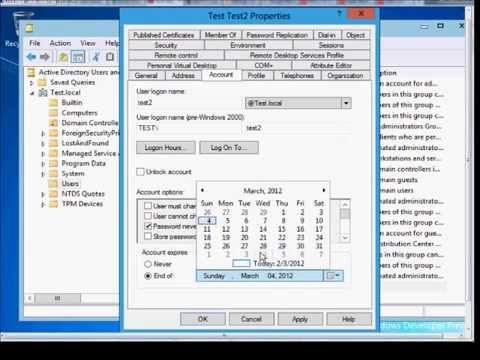
Powershell Set Account Expiration Date
User accounts for vendors or contractors are often needed only temporally, but even if the IT team sets an expiration date, a malicious actor can reset the date by running a simple ADAccount cmdlet and then use the account as a backdoor to gain access to IT systems like Windows Server and Microsoft Active Directory.
Powershell command to Configure Password Never Expires flag:
The Identity parameter specifies the Active Directory user to modify. You can identify a user by its samAccountName, distinguished name (DN), GUID and SID.You can select AD users from specific OU and set as password never expire users by using Get-ADUser and Set-ADUser cmdlets. You can set target OU scope by using the parameter SearchBase in Get-ADUser cmdlet. This following command select and set as password never expires flag of Active Directory users from the Organization Unit 'TestOU'.
You can filter sepecific set of AD users by using SQL like filter with Get-ADUser, users who are not familiar with LDAP filter can easily use this filter to get only specific set of AD users
You can also use LDAP filter with Get-ADUserpowershell cmdlet with more flexibility to filter Active Directory users.
You can read Active Directory from csv file using Powershell cmdlet Import-CSV. Consider the CSV file ADUsers.csv (Ex file: Download ADUsers.csv) which contains set of AD users with the attribute samAccountName.
You can set password never expires flag for only specific Active Directory group members by getting AD group members using Get-ADGroupMember cmdlet. The following powershell script select all the members 'TestGroup' group and set as password never expire users.
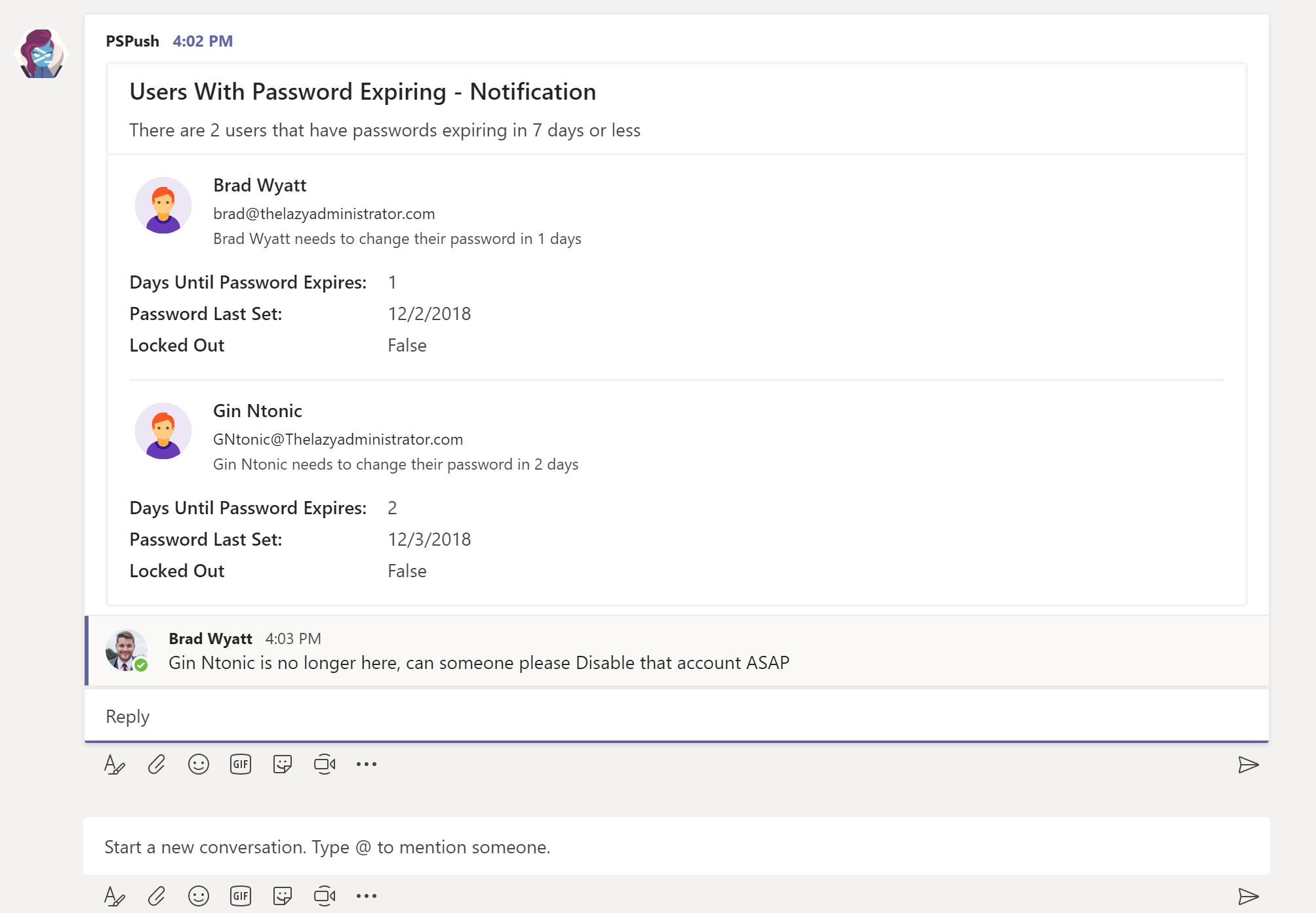
Few weeks ago I came across this question “How to find out an account’s password expiration date” in one of our internal mailing-list. This looks like a simple question, but when we tried to find the answer we realized it is not a trivial task. One of my colleagues pointed to this 22-printed page detailed MSDN article that describes how to find a user account’s password expiration date. The steps described in this article are a bit outdated. It does not take Fine-Grained Password policy (a new feature added in Windows 2008) into account while calculating the maximum password age. With the addition of fine grained password policy, this becomes an even more daunting task to do. Using AD Powershell this task can be achieved with ~40 lines of script-code. Here is function that calculates the password expiration date of a user object given its samAccountName, security identifier or DistinguishedName.
Here are some sample usages of this function:
Since the MSDN article explains the algorithm using a flow diagram, I too have tried creating a flow diagram that explains the logic used to compute the password expiration date of an account:
Set Ad Account Password Powershell
Hope you find this useful. Please leave a comment if you have any feedback on this topic or would like to see any other topic discussed in our blog.
Enjoy,
Swami